Hacktivists and the Dark Web: protecting infrastructure from cyberattacks

This article was previously published in our newsletter, if you're not already a subscriber, sign up here.
By moving our lives online in response to the pandemic, we have unleashed a boom in ecommerce, video conferencing and mobile gaming...but also, unfortunately, in cybercrime. The FBI says cyber security complaints in the US have more than tripled from pre-COVID times to nearly 4,000 a day. Meanwhile, a McKinsey survey predicts that damage from cyberattacks will increase to $10.5 trillion annually by 2025 -- a 300% increase from 2015 levels.
Not only are there more attacks; they are becoming more sophisticated. Clumsy email phishing expeditions are being replaced by cleverly orchestrated attempts to implant malware or ransomware. Hackers can operate from virtually any country, making them almost untraceable; and, increasingly, they are using automated bots to reinforce their attacks and freeze or overwhelm whole networks.
In fact, hacking has become a career, often a lucrative one. The single, politically motivated hacker of the 1990s has been replaced by organized groups of 'hacktivists', who select well-resourced commercial targets: like the Colonial gas pipeline that was closed by a cyberattack in May 2021. Ransomware as a Service (RaaS) is for sale on the Dark Web, allowing today's hackers to purchase a subscription to already-developed ransomware tools -- much like you and I buy a subscription to Netflix.
Never trust and always verify
Fortunately, our defenses are improving too. Since the main weak points in any attack are people -- too often careless, forgetful and lazy, even if not actually malicious -- modern cyber security is beginning to operate on the principle of 'zero trust security'.
Conventionally, companies maintained a clear boundary between their systems and the outside world; if a hacker tried to penetrate this it would trigger an alarm and a set of defenses. Companies have relied on such perimeter security strategies, which typically use network-based tools or equipment such as a firewall to monitor the boundary of the network. Such perimeter security is effective in keeping attackers out of the network but vulnerable to internal 'bad actors'.
The zero trust approach, by contrast, requires every user or device to prove that they are not attackers, even if the user or device are already inside the network, making use of modern technologies such as two-factor authentication. This provides advanced threat protection as the boundaries between work and home disappear and an increasingly distributed, remote workforce becomes the norm.
While such a rigorous protocol is safer, it is also more burdensome. It demands that all network or system activity is monitored: Who is this user? What systems are they accessing? What data are they trying to download? It takes a sophisticated, high-capacity software system to be able to collect and interpret all this data.
This is what Mitsubishi Heavy Industries (MHI) Group has developed with InteRSePT, our dual-use cybersecurity solution to protect critical infrastructure such as power plants and major manufacturing facilities, as well as defense equipment from ships to unmanned vehicles to entire military bases.
Watch that behavior
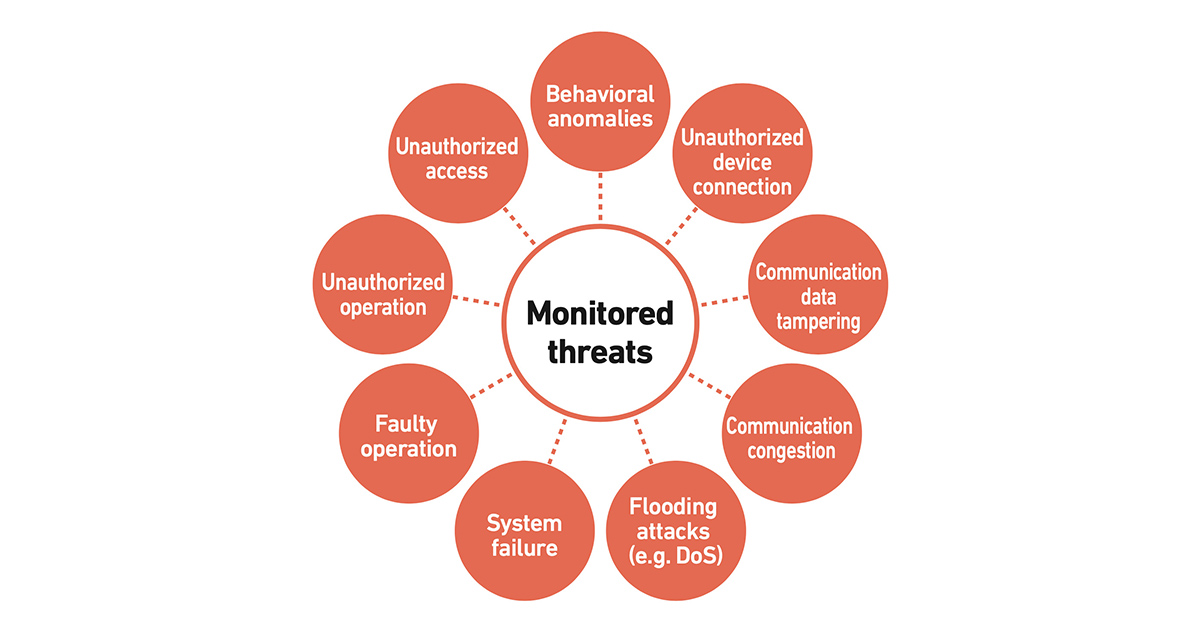
InteRSePT monitors activities on the target network (say, the operational control system of a factory or the guidance system of a drone) and will detect suspicious network communications or network devices and alert an operator. However, there are a number of products that can do such network monitoring. What really distinguishes InteRSePT is that it also analyzes the behavior of the system and all its users, according to specific rules tailored to each customer. Such behavioral anomalies also trigger an alert -- for example, a regular network device sending an unusual command to a plant.
MHI's ability to craft specific behavioral rules for individual customers is based on our deep familiarity with their habits built up over years of working together. This partnership approach is one we follow across the group: another example is our TOMONI service, which monitors the operations of customers' power plants on their behalf.
Such close cooperation gives MHI an inbuilt advantage when it comes to designing solutions to guard against cyberattacks -- especially those from within. This was a key rationale behind the development of InteRSePT, which is in operation with a branch of the Japanese government. Demonstration models are currently being tested with a range of commercial customers. And we are also rolling out the system across MHI's own factories.
As major energy, utility and manufacturing firms have started to shore up their cyber defenses, the hackers have turned their attention to the smaller companies making up their supply chains, many of which cannot afford top-level protection.
That is prompting MHI to design more basic, lower cost versions of InteRSePT. We are currently doing concept studies for both a portable model that can run on a laptop and be transported in a briefcase; and an even smaller one that could, for example, be embedded in a drone or other unmanned vehicle.
Cybersecurity is like a giant game of chess, with the hackers and defenders trying to outwit each other. We are always trying to anticipate their next move and refining our defenses to make them more resilient. We know the hackers will not give up, but neither will we.
Discover more about MHI's Cybersecurity Solutions